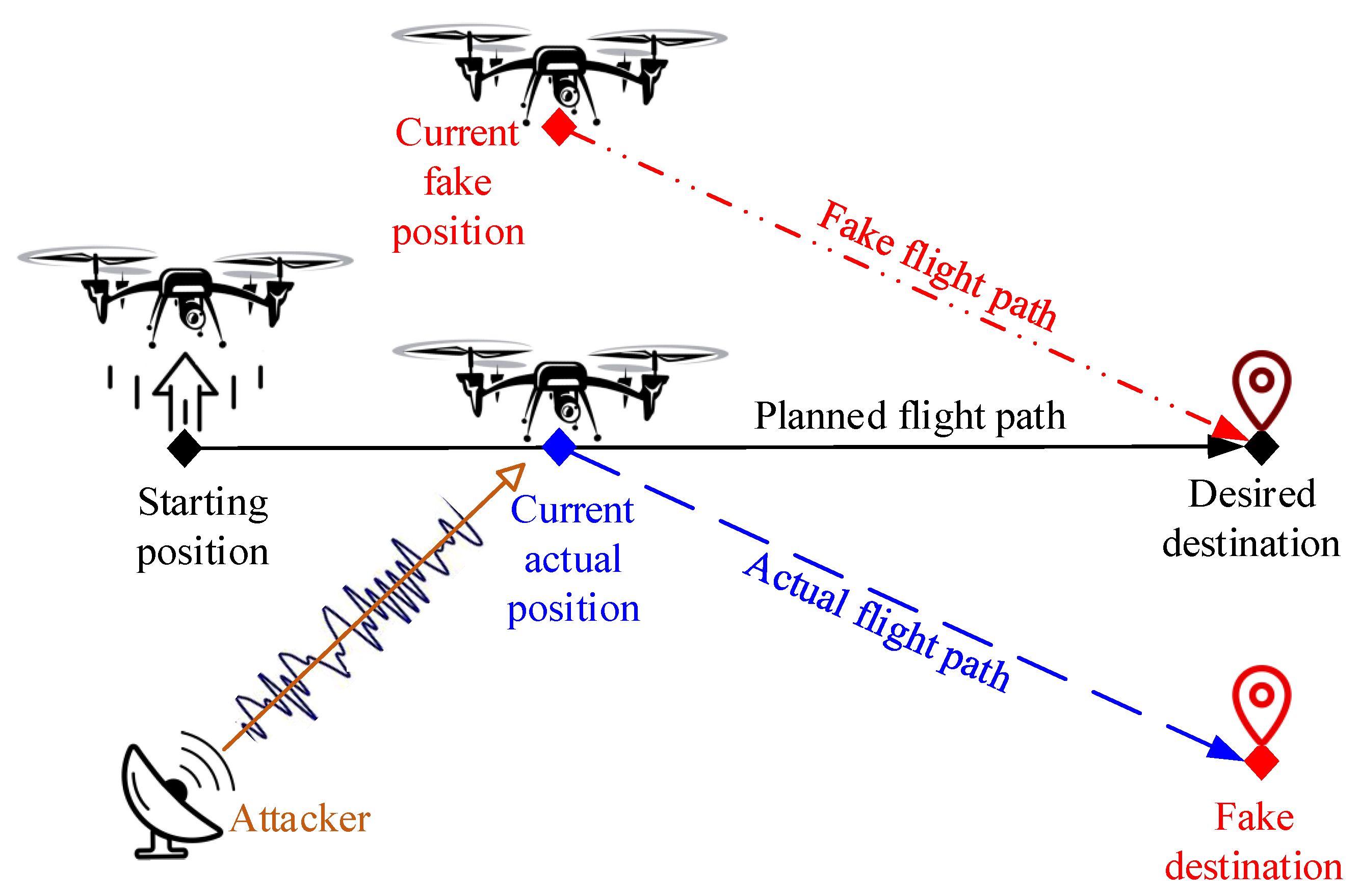
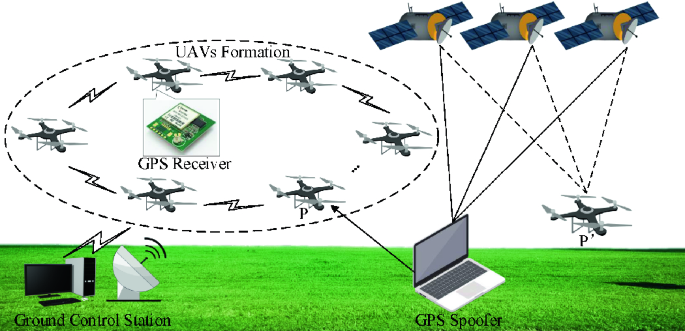
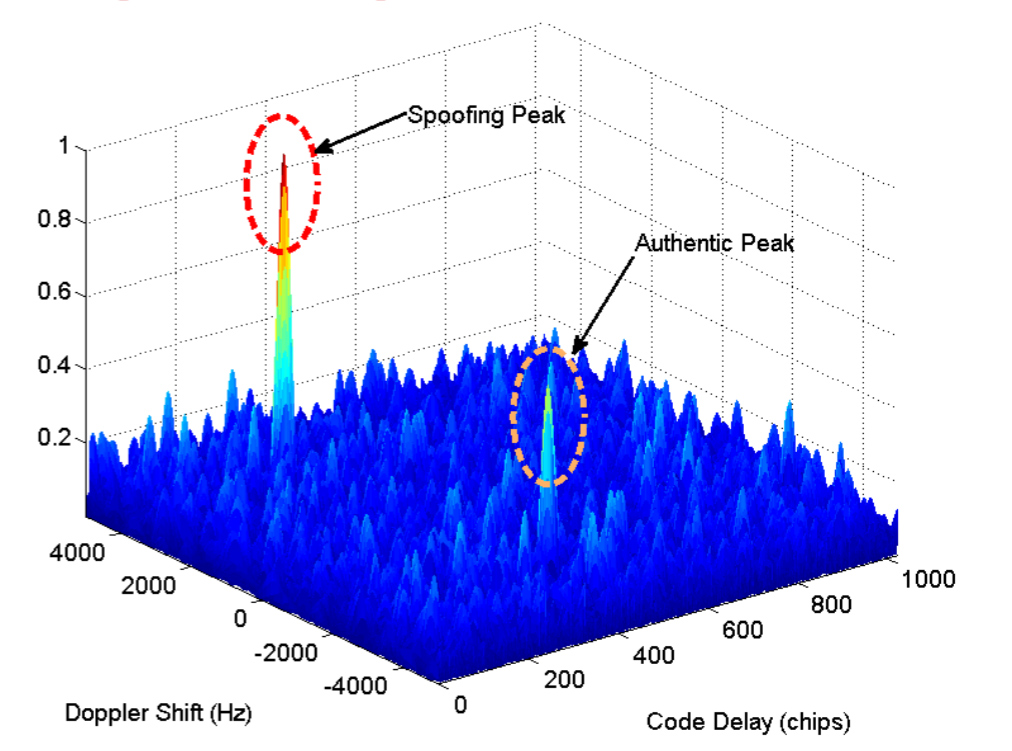
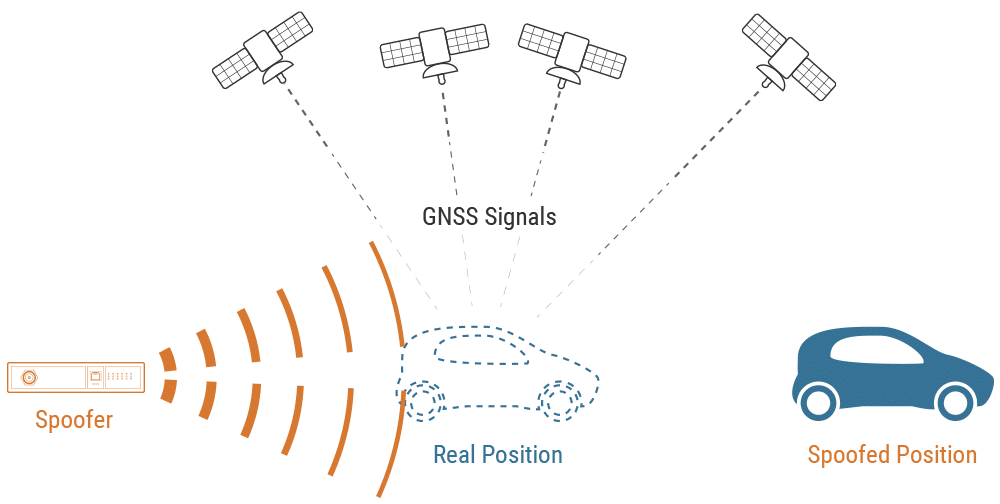
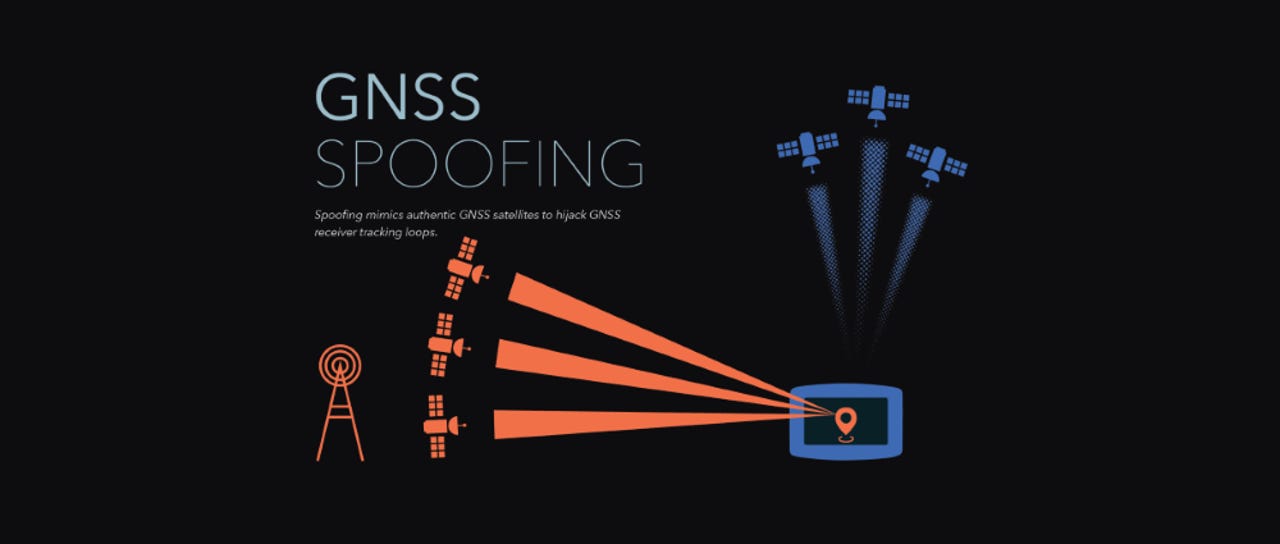
![On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ] On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2021/cs-507/1/fig-4-2x.jpg)
On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ]

Drift with Devil: Security of Multi-Sensor Fusion based Localization in High-Level Autonomous Driving under GPS Spoofing | Synced

AuthGPS | Proceedings of the 17th Annual International Conference on Mobile Systems, Applications, and Services

Analysis of effect of anti-spoofing signal for mitigating to spoofing in GPS L1 signal | Semantic Scholar